Migrating workloads to the cloud has benefited enterprises by increasing the speed and scalability of their data and operations and enhancing user experience. Now, discussions in corporate boardrooms revolve around compromised data protection and data privacy. While cloud adoption simplifies life by providing greater functionality, it also complicates life by increasing the threat vectors and making end-to-end security harder to deploy.
Many organizations today are cautious about storing their critical data in the public cloud. Securing cloud instances depends on a well-defined, shared responsibility model between the enterprise (tenant) and the service provider based on whether the workload is hosted on software-as-a-service (SaaS), platform-as-a-service (PaaS), infrastructure-as-a-service (IaaS) or in an on-premises data center. While the “share” in “shared responsibility” indicates that both parties (provider and customer) have duties to fulfill in the model, accountability is still with the customer to ensure due care happens. This is because the customer owns their data.
Misconfigurations in the Cloud
Misconfigurations are one of the largest, if not the largest, security risk for cloud environments. Without the right controls, they are easy to create and tough to detect. The speed at which cloud resources can be spun up also creates ample opportunity for missteps and cut corners. Many have heard about the horror stories of privileged credentials and keys being stored in public-facing, open-storage services. That’s one example in which the desire for speed and convenience comes back to bite hard.
The work required to set up public cloud environments allows for the rapid collapsing of skillsets. To be really good at configuring workloads in a public cloud, you have to be good at networking, infrastructure and security. It’s often software developers and application teams who adopt cloud before other teams; if they aren’t experienced or properly supervised as they design the cloud network and infrastructure with the appropriate permissions and access controls, it will likely lead to rampant security concerns and surprisingly high consumption costs.
Many of the organizations that are experiencing this type of scenario and are aware of the dangers have started to focus on cloud security posture management tools. These tools provide crucial visibility for security operations teams with two major types of vulnerabilities: 1) those that require patching, like an outdated version of software, or 2) misconfigurations, such as a VM unintentionally exposed in a public-facing subnet.
The Problem of Visibility in Cloud Security
Think about this: we are now at a point where an organization’s data is often sent cloud-to-cloud without passing back through the customer’s on-premises network. This creates real problems with visibility when it comes to cloud security. Cloud environments are fluid, scalable and beyond the boundaries of our corporate networks; cloud security is a matter of enhancing visibility and building new boundaries where there are none.
We hear about Zero Trust as a buzzword that’s often tossed in conversations around cloud security transformation, but a real first step is building boundaries around, within and between our cloud environments. This happens through segmentation with the right tools and services that can monitor and control north/south and east/west traffic between and within those segments.
Cloud Transforms Fast, Cloud Security Must Too
To complicate the fluidity and scalability of cloud environments, the services used within them are everchanging. New services become available very often, and securing those new services is a constant game of chase. Tools and best practices for API security, serverless and function security, container security and infrastructure-as-code security, etc. must be key areas of focus for organizations as they are becoming more prevalent in workloads and services.
The Metastructure Layer
As enterprises rely more and more on the cloud, security controls must be organized and mapped to different layers. One of the key deterministic attributes of cloud is what is called the “metastructure layer.” While application security is managed at the applistructure layer, data security is managed at the infostructure layer, and infrastructure security is managed at the infrastructure layer, it is the metastructure layer in cloud security that provides the interface between the infrastructure layer and all other layers. This layer is often called the “management plane” for cloud environments.
Figure 2 below illustrates these layers and their corresponding security control levels. A key difference between cloud security and traditional computing security is at the metastructure level. Services at the metastructure are network-enabled, remotely accessible and often provide security testing for cloud providers as well as the customers.
Cloud service providers (CSP), who routinely attest to adequate security operations in protecting their systems, also play a pivotal role in identifying how much detail must be revealed to prevent misconfigurations that can disrupt service and impact the availability of tenant environments.
The metastructure can be considered the cloud service provider/customer line of demarcation (a.k.a. the “waterline”). Above this waterline, cloud consumers must implement cloud applications to securely utilize the cloud platform and underlying services. Everything underneath the waterline is the CSP’s responsibility to secure. Regardless, because this layer contains management and control functions, it requires strong hardening techniques to enhance the security posture.
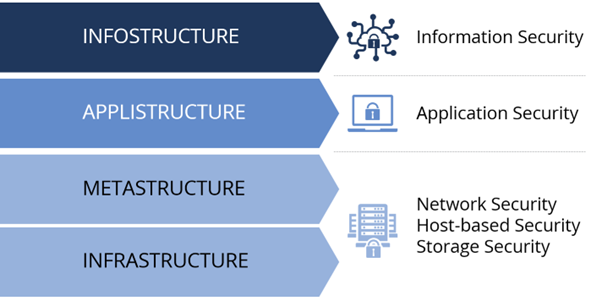
Figure 1: Dissecting Cloud Layers
Guarding the Metastructure
Since many of the latest risks revolve around misconfigurations and authentication, enterprises must ensure they have clear visibility and control at each layer above the “waterline.” Many of the emerging digital native and digital immigrant firms that have adopted cloud still implement security as an afterthought. Speed to market is their primary focus, and security is often overlooked.
To avoid misconfigurations and secure protocols and mechanisms involved at the metastructure level, companies must avoid applications that are not cloud-ready or designed for cloud environments. In many cases, the “lift and shift” approach that advanced initial cloud adoption is forcing many enterprises back to the drawing board to re-architect applications that leverage advanced cloud services. This effort will move many of the security controls in the secure application development lifecycle up the layer stack illustrated in Figure 2.
Still, enterprises are struggling to close security gaps that are higher in the technology stack because they are more nuanced and specific to data and application controls. Binding security controls to application development lifecycles (such as CI/CD pipelines) can help close those gaps.
The transition to the cloud requires implementation of an appropriate security architecture and embedded security to withstand cyber-attacks and provide appropriate safeguards as early as possible in the design phases and throughout the process.
ISG helps enterprises detect and prioritize misconfigurations and enhance cloud security visibility. We offer expert consulting services to help clients devise security methods, controls and procedures at the build stage and to develop cloud strategies that account for the most common misconfigurations and vulnerabilities when migrating to and running cloud environments. Contact us to discuss how we can support you.
