If we look at the past year, we see that attacks from state threat actors have increased rapidly, making cybersecurity the world’s largest and most innovative crime sector. In Germany alone, according to a recent study from Bitkom, cybercrime has cost companies around 203 billion euros.
ISG Research shows that the percentage of IT spend that most organizations are allocating to cybersecurity has been on the rise. In 2019, most organizations were spending 7.5% of their IT budget on cybersecurity. In 2022, cybersecurity amounted to 9% of overall IT spend, which means companies increased their cybersecurity budget by around 8.7% a year.
Cybersecurity Spend Is on the Rise
In Germany, the amount of investment in cybersecurity (8.4% of IT spend) is increasing as well, but small and mid-size organizations still face challenges getting results from their budget. In other words, small and medium-size organizations want the “biggest bang for the buck” and are reluctant to increase investments in cybersecurity. If we look at sectors that are highly regulated like Banking and Financial Services, cybersecurity investments are increasing by a factor of two, while Retail companies’ investments have not changed significantly over the past years.
Figure 1 shows increased IT spending on cybersecurity in Germany; Figure 2 shows overall investment in cybersecurity in Germany.
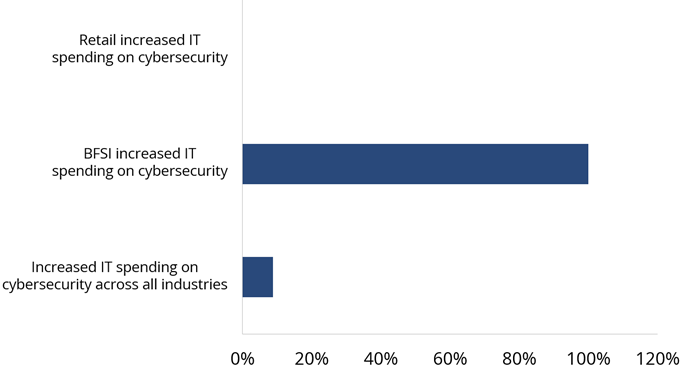
Figure 1: Increased IT spending on cybersecurity
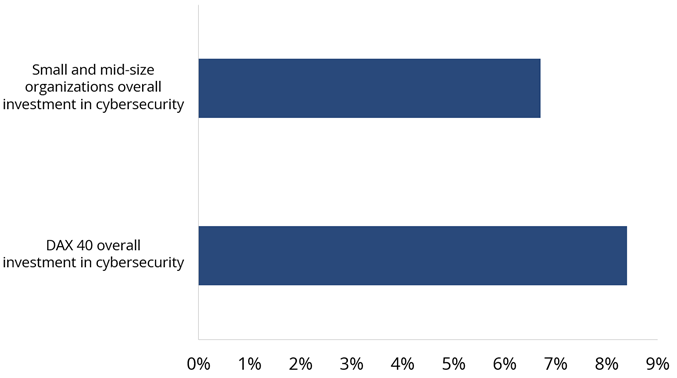
Figure 2: Overall investment in cybersecurity
Cybersecurity Spend Does Not Equal Greater Results
ISG Research also shows that cybersecurity investments are not directly related to an organization’s improvement in overall risk/security posture. Conversely, research shows that buying multiple tools often increases noise and reduces the overall efficiency of an organization’s security capabilities.
Irrespective of their size, organizations in EMEA have implemented cyber or information security policies and regulations in the form of an information security management system (ISMS) based mostly on ISO standards. The purpose includes pleasing auditors and regulators and achieving certifications (ISO 2700X, BSI C5, etc.) to boost business. Only a handful of organizations can claim they have successfully realized a return on the implemented ISMS. Others have either made the implementation too complicated or used a fragmented solution. Policies are either simply copied together or not integrated into the company’s ecosystem. They are discussed once and then never touched again. The risks arising from this are significant.
According to ISG Research, ISMS implementation maturity is low in the current market; we have found that more than 75% of organizations in EMEA have implemented a static ISMS, which only creates extra manual work in terms of assessments, interviews, evidence gathering and management. The actual value that needs to be realized from an ISMS is far from where it should be.
One reason is that a mature ISMS is a labor-intensive effort. A conference paper published by IBM states that employees can no longer manually carry out cybersecurity processes due to increasingly complex requirements and growing threats. Some organizations are looking into “compliance-as-code,” in which adherence, application and remediation of compliance controls are automated. We also know of examples in which artificial intelligence is reducing the human effort in cybersecurity while maintaining or even increasing the level of security.
Current Market ISMS and Challenges
An ISMS is all-encompassing and involves different cybersecurity areas: communication, roles and responsibilities, risk management, identity and access management, etc. Many companies believe once they have implemented an ISMS, they have a solid foundation for security forever and against all anomalies. Our experience shows that this is not usually the case.
With all our clients, whether they are medium-sized or large corporations, we regularly find that their ISMS consists of countless, static documents that, due to their extensive numbers, are difficult to keep current on a regular basis. If specific content is required by a user, admin or developer, the challenge is to find the right answer. However, this content usually lacks target group specificity and specific work instructions can rarely be derived from it. In our experience, this often leads to individual employees creating specific work instructions "on their own." Since this is not a standardized process, these results are rarely recorded centrally and made available to other colleagues. In the worst case, another colleague also creates documents on his or her own, resulting in avoidable duplication of effort.
This is just one of the countless examples we encounter every day. It is not enough to merely meet the minimum requirements of ISO 27001 certification, for example. To achieve true growth in security, it is necessary to integrate an ISMS into the company and development processes – but without tool support, this is virtually impossible. Moreover, the CISO or ISO must satisfy the needs of all stakeholders at once, which often creates a bottleneck (see Figure 3).
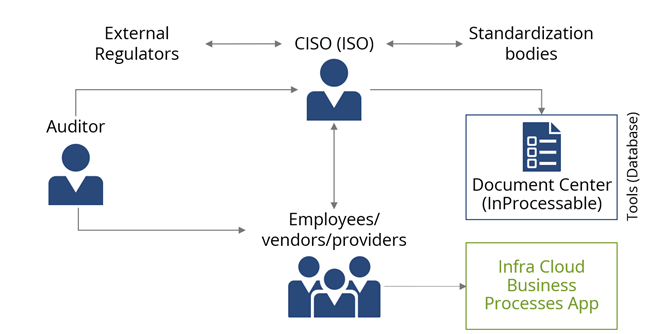
Figure 3: Outline of a typical CISO/ISO ISMS responsibility
Due to the increasing importance of cybersecurity in public and private organizations, it is important not only to implement an ISMS for the purpose of certification but also as a way to:
- Keep an existing ISMS up to date and effective with less (manual) effort.
- Make an ISMS available to stakeholders in the required format, including specific work instructions.
ISG Policy Align
In our cybersecurity consulting over the past several years, we’ve seen that ISMS implementations, revisions, and outsourcing are among the most frequent client requests. The challenges we most often see with an ISMS include:
- They are static and document-based with documents that are written but not “lived” and too long to kept up to date.
- They use suboptimal communication with documents that are not written in plain language therefore known only to the CISO, who ends up being a bottleneck.
- They lack integration of the corporate environment, processes and tools. Dynamic ISMS documentation and easy-to-understand instructions for the appropriate target group could be great improvements.
ISG offers an ISMS solution that covers all three of the above challenges. We have partnered with a developer to create software that uses machine learning and artificial intelligence to compare individual client policies with specifications and standards, such as ISO 27001 or the German BAIT and VAIT. This can significantly streamline the process of adapting corporate policies in response to updated regulations.
In our next POV in this two-part series, find out how you can benefit from our future ISMS developments. Contact us to learn more.
