In June of this year, the U.S. Department of Energy released a conceptual framework for protecting the nation’s critical infrastructure. It’s called the National Cyber-Informed Engineering Strategy. The release arose from the U.S. government’s need to protect the country’s critical infrastructure from growing cybersecurity risks. Though the principles proposed in the framework are not new, they should be taken seriously.
In short, “security by design” is the driving message, and rightly so. Many organizations have critical infrastructure in their operational technology environments that were designed to operate functionally but that lack awareness and accounting for cybersecurity risks. For example, in the oil and gas sector, a variety of equipment and systems from the wellhead to interstate pipelines, new and old, were not designed with security in mind. It is important for companies across the energy industry to identify and prioritize the assets at highest risk and implement cybersecurity protections via a framework like Cyber-Informed Engineering.
Six Core Principles for Cyber-Informed Engineering
The Cyber-Informed Engineering framework includes six core principles. The concepts are not surprising or new, but incorporating them into practice is paramount.
- Consequence-focused design: ensure the design of critical infrastructure systems takes into account the possibility of the components being manipulated and the likelihood and impacts of those manipulations.
- Engineered controls: include safeguard and countermeasure controls in the upfront design phases of the systems to address and reduce the risks to acceptable levels.
- Secure information architecture: architect the data and information storage and flow of the systems to ensure confidentiality, integrity and availability.
- Design simplification: avoid making the systems and components unnecessarily complex.
- Resilient layered defenses: make sure the system has layers of controls that defend its security posture and that the layers are independent of each other (not co-dependent) and cannot be sidestepped.
- Active defense: design the defenses to provide “active” alerting and detection capabilities.
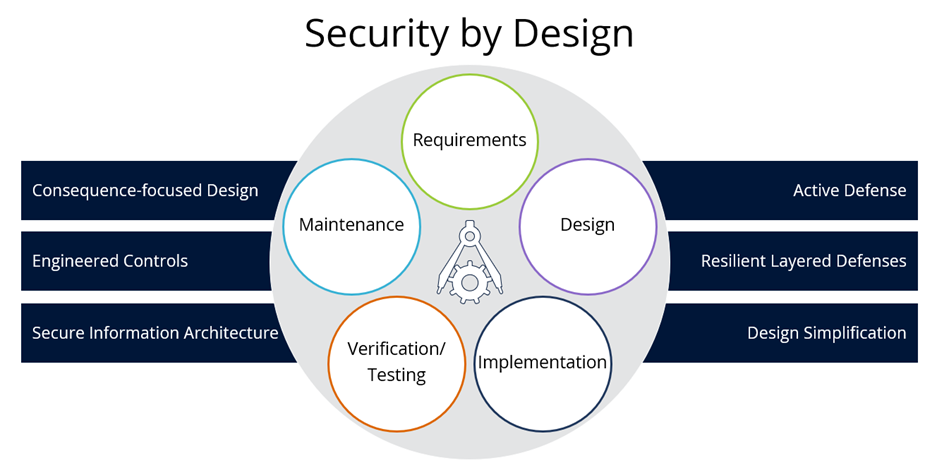
Figure 1: Cyber-Informed Engineering Principles
The figure above shows how the six Cyber-Informed Engineering principles can be overlayed onto the standard security-by-design process. The good news is that organizations can use the principles to achieve the right outcomes in each phase of the cycle. This is a strong framework to adopt for go-forward critical infrastructure systems design.
Organizations can also adapt this framework to account for systems that were not implemented with security by design principles. Depending on the risk levels, there may be a need to redesign various components or replace the systems all together.
The Department of Energy’s Cyber-Informed Engineering framework and strategic plan can be found here. ISG helps companies across industries understand and apply best security practices to keep their critical infrastructure safe. Contact us to find out how we can help.
