For years, organizations have been prioritizing their digital transformation efforts, sourcing software-as-a-service solutions and deploying cloud-based applications to increase agility and improve customer experience. And while these efforts have certainly brought about those benefits, they also have increased companies’ exposure to the cybersecurity risks that come with increased interconnectivity and data-sharing. The well-known and countless lesser-known cyber breaches serve as cautionary tales.
Legacy technology, cloud adoption and an explosion of internet-facing devices and services are overwhelming IT and security organizations, many of which are not equipped to keep up with basic vulnerability management practices in hybrid environments. The reality is many organizations still rely on legacy approaches to IT cybersecurity. These are typically reactive and perimeter-bound and don’t always take into account hygiene errors – made more common by hybrid-cloud configuration – which are a major cause of breaches. These issues coupled with the supply chain vulnerabilities and increase in nation-state threat actors are driving increased demand for cybersecurity solutions and services.
Increased Spending on Cybersecurity Solutions
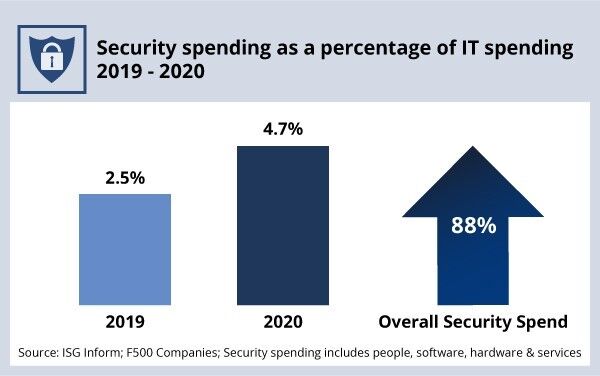
According to recent ISG research, enterprise security spending per user increased by more than 40 percent between 2019 and 2020 – and is likely to increase again in 2021. As a percentage of total IT spending, cybersecurity nearly doubled year over year, accounting for 4.7 percent of spend in 2020, versus 2.5 percent in 2019 (see figure below). Nearly three-quarters of ISG advisors say their clients plan to increase their security spending this year, and that was even before the unprecedented SolarWinds and Exchange breaches in the first quarter.
The Challenge of Building a Cybersecurity Solution
Even with increased spend, architecting and adopting a cybersecurity solution that is flexible enough to support both a legacy environment and digital initiatives is an immense challenge. And, because most security breaches are connected to insiders, the supply chain or supplier ecosystems, a company’s vulnerabilities now exist inside the perimeter and expand in widening circles outward from their IT environment.
This is why most companies struggle with disconnected cybersecurity governance, risk and compliance frameworks, which can create a significant gap between knowing and doing. This gap makes it difficult to reconcile a security strategy with the execution of a sound enterprise-wide cybersecurity program.
In the meantime, the IT services market is responding to the increased demand for cybersecurity services, which makes for a dynamic provider landscape. Some providers are organically building next-generation cyber services, and some are acquiring them. Just in the first quarter of 2021, Atos acquired Motiv ICT and In Fidem, Deloitte acquired R9B, and Wipro acquired Ampion. We expect to see more M&A in this space this quarter and in the year to come. As these and other providers expand their portfolio of offerings, it’s important to remember that providers become part of your supply chain and are not immune to cyber breaches themselves.
Assessing Your Cybersecurity Capabilities and Maturity
Many organizations are not sure where to start. They have some tools and services in place but aren’t confident that their maturity, operational delivery and culture of security services are sufficient to protect their enterprise.
The ISG Cybersecurity Effectiveness Assessment uses industry-leading practices to assess your cybersecurity posture and security provider ecosystem. We help enterprises improve their cybersecurity program in six steps:
- Analyze security operating models and governance programs; identify opportunities to reduce vulnerabilities by up to 95 percent.
- Review and analyze current controls, functions and policies against industry-standard cybersecurity frameworks such as NIST-CSF, ISO and CIS.
- Identify gaps and build roadmaps, including provider ecosystem requirements, to reduce risk and increase cybersecurity program maturity.
- Leverage industry-leading cybersecurity financial and operational benchmark data to compare your cybersecurity investments and performance to peers and the market.
- Calculate the investment required to execute on your cybersecurity strategy and build a more secure enterprise culture.
- Apply provider and market insights to operationalize security; use our unparalleled data and expertise on the security provider ecosystem to operationalize security strategies and roadmaps.
Cybersecurity is too important to bolt on as an afterthought. We help organizations leverage providers in the market to deal with commodity security functions and free up your cybersecurity leadership and engineering resources to regain strategic advantage. Contact us to find out how we can help you assess where you are today and where you need to go.
