Cybersecurity investments are different from business-driven investments. For business-driven investments, it is useful to measure the expected output (the amount of revenue) against the required input (the amount of investment). If there is a positive figure that meets the company´s investment target or higher than other investment options, the decision is easy to make.
For cybersecurity, there is no expected revenue against which the required investment can be measured. So how can decision-makers decide which investment should be prioritized, especially in times of limited resources?
Cyber Risk Quantification Use Cases
Cyber risk quantification supports decisions regarding cyber investments by assigning financial value to specific cyber risks. This allows decision-makers to prioritize and sequence cyber initiatives based on the expected cyber risk reduction compared to the required investment or by choosing initiatives that have the quickest expected impact over time.
Cyber risk quantification measures the cyber risk reduction of cyber programs over time by recalculating cyber risk when additional cybersecurity measures are implemented. It compares the target and the actual risk reduction to measure progress along the way. It is useful in cyber program planning as the cyber risk exposure can be calculated for various dates, tracking the overall cyber risk reduction over time.
Cyber risk quantification provides a business case for a cybersecurity initiative, outlining how the required investment will pay off against the related risk reduction. It also plays an important role in insurance coverage by evaluating whether the planned or existing cybersecurity insurance coverage is sufficient or needs to be increased.
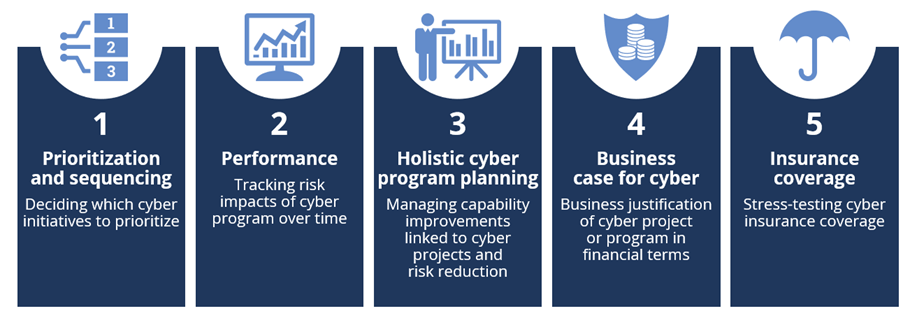
Figure 1: Practical Use Cases of Cyber Risk Quantification
Cyber risk quantification supports effective decisions at the board level and translates the cyber resilience into commercial terms. It gives the CEO, the CIO, the CRO and the CISO a common language – and it provides other members of the cybersecurity team a way to turn technical and organizational measures into dollars or euros.
The Cyber Risk Quantification Approach
Cyber risk quantification is performed in a series of workshops with a diverse group of participants from different departments in the organization, such as IT, the business and information security. This is important for avoiding blind spots.
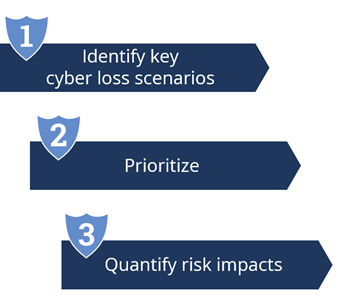 Figure 2: Key Steps to Quantifying Risk Impacts
Figure 2: Key Steps to Quantifying Risk Impacts
The second step is to prioritize these scenarios. This can be done by voting, forced ranking or by top-down influence from the board or an executive leadership team. Start by quantifying five to ten scenarios and add further over time based on the company´s need and available resources.
The third step is to quantify the risk impact. Include the financial impact (including the intangible impact, such as reputation, which needs to be translated into financial impact) and the physical impact on the company as well as on third parties (such as suppliers or customers). The result is the expected loss exposure for each scenario. If the estimation is done with minimum and maximum values per formula component, the total loss exposure will provide a total minimum and a total maximum in addition to the expected loss exposure for each scenario.
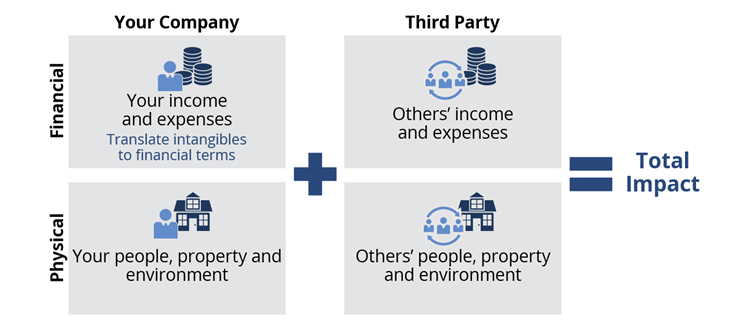
Figure 3: Cyber Risk Quantification: Calculating the Total Impact
ISG helps enterprises quantify their cyber risk so they can make smart cybersecurity investments and prepare for the future. Contact us to find out how we can help you get started.
