As technology evolves, organizations are facing new challenges in protecting their endpoints from emerging threats. The shift toward cloud computing and the rise of internet-connected devices renders the existing perimeter approach no longer sufficient to meet today’s security challenges. Companies need to know exactly what the threats are to their infrastructure. Mandiant reported a median dwell time of 33 days in EMEA, giving attackers a long timeframe to compromise the network and exfiltrate data.
What Is EDR?
Endpoint detection and response (EDR) solutions can help address this challenge. EDR solutions enable an organization’s security team to monitor and detect advanced threats and malicious activities on laptops, servers, mobile devices and cloud workloads. This is done by leveraging the additional telemetry data provided by the EDR, like log data about suspicious behavior or potential malware. This enables security operations centers (SOCs) to provide enhanced detection, investigation and response capabilities to improve near real-time visibility and limit the scope and financial impact of security incidents.
Choosing the right EDR solution can be a daunting task given the multitude of options available on the market and the different dimensions to consider. Nevertheless, choosing the right product and the right service is essential.
A well-executed EDR sourcing engagement will result in the following:
- A comprehensive view of capabilities and potential bottlenecks that might otherwise limit the SOC.
- Mitigation of operational costs and risks through an adequate assessment of the different solutions.
- Selection of a best-fit solution to reduce the probability and the impact of security incidents.
Three Dimensions to Consider when Selecting an EDR Solution
When selecting the best-fit EDR solution, three key dimensions play an important role: sourcing transaction, industry reports and technical testing. The consideration of these dimensions is essential in making an informed decision.
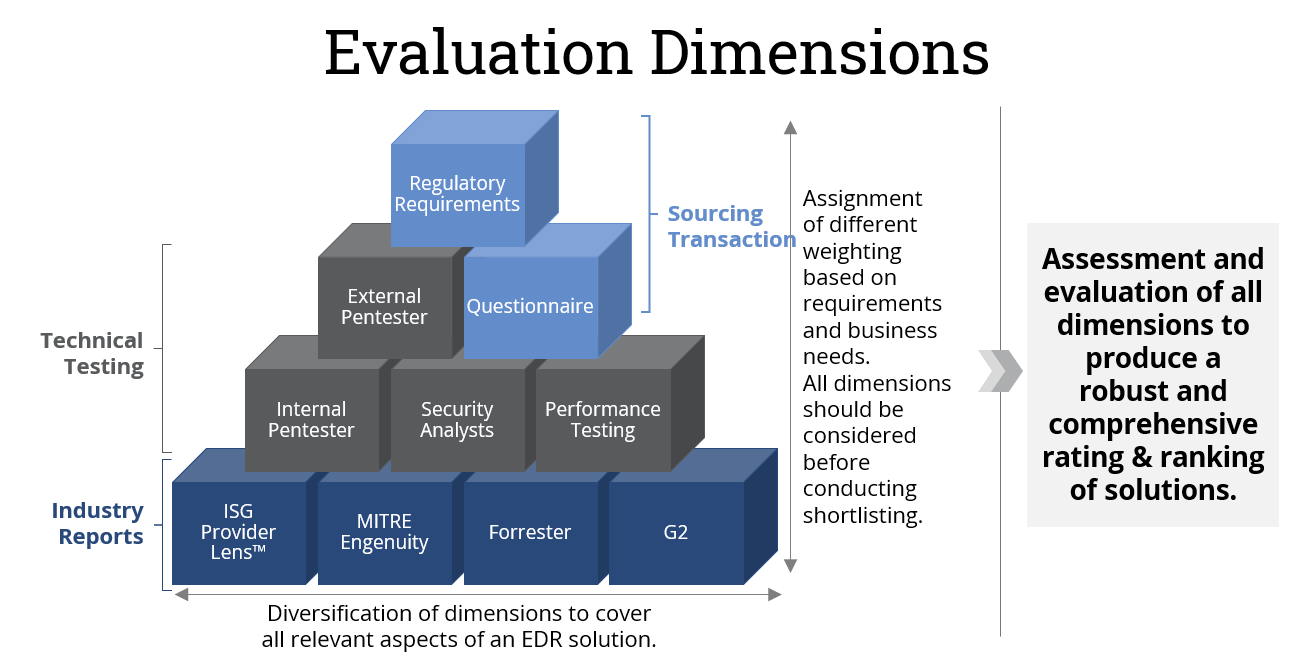
- Sourcing transaction
The sourcing process allows your organization to gather comprehensive information from potential solution providers, ensuring that all relevant requirements and expectations are addressed. The process includes a questionnaire to various vendors to verify they can meet regulatory requirements. Visibility into vendors’ capabilities to meet must-have, should-have and optional criteria ensures a fair and transparent decision-making process.
- Industry reports
Industry reports provide valuable insights into the performance, capabilities and reputation of EDR solutions. ISG Provider Lens™ reports are among the best reports that provide independent assessments based on extensive research, customer feedback and comparative analysis of solutions and service providers. Incorporating industry reports into the evaluation process allows you to gain a broader perspective, make informed decisions based on expert analysis and compare EDR solutions on the market against self-designed technical tests.
- Technical testing
Technical testing involves a thorough assessment and evaluation of the technical capabilities of each EDR solution, focusing on the individual requirements and target environment. This includes setting up test environments and performing relevant tests. This can range from internal or external detection tests, performance tests to assess the impact on endpoint resources or usability tests conducted by security analysts. As these are tailored to the specific environment, they provide a better understanding of detection accuracy, false positive rates, response time, scalability and compatibility with existing infrastructure.
The Importance of a Structured Sourcing Transaction
Selecting a powerful EDR solution is challenging but also critical for organizations seeking to strengthen their security posture. By evaluating potential solutions across multiple dimensions and conducting a thorough technical analysis, organizations can make an informed decision based on their specific requirements and business needs. When evaluating and running sourcing engagements for EDR solutions, be sure to keep the following in mind:
- Strategic alignment
- Efficiency in decision-making
- Improved partner selection
- Faster contract signing
The ISG FutureSource™ methodology allows you to align your sourcing strategy with your business objectives and needs, enabling you to capitalize on the latest EDR capabilities. Additionally, our methodology ensures you can consolidate and evaluate options in an ever-expanding provider marketplace, selecting the best-fit partner for your specific needs.
The methodology's streamlined and proven approach reduces the time it takes to sign a sourcing contract, allowing you to start benefiting from the chosen solution promptly, while reducing unnecessary overhead during the evaluation.
ISG’s expertise in cybersecurity, visibility in the market via ISG Provider Lens™ and our FutureSource™ approach give enterprises an excellent starting point to identify the best possible solution. Contact us to find out how we can help you get started.
